won apos t take my ad

Tài liệu Mission-Critical Security Planner When Hackers Won’t Take No for an Answer doc
Ngày tải lên :
24/01/2014, 14:20
... organization’s system Often the best way to deal with such attackers is to give them the attention they seek; that is, give them your full attention, as opposed to giving an attacker the opportunity ... numbers—at the same time, they don t want to take out their calculators Adding four numbers that total to 100 (in the worst case) tends to work best when factoring in the realities of the process ... provocative with malicious attackers, nor you want them to see you panic This is the reaction they’re hoping for The best tactic is to distract them so that they believe you are taking a direction that...
- 433
- 563
- 0

Mission-Critical Security Planner When Hackers Won’t Take No for an Answer phần 2 pdf
Ngày tải lên :
13/08/2014, 22:21
... implementation laboratory is not connected to the network at large Another important aspect of implementation is testing—that is, verifying that the plan works as expected and that the technology ... code signing, that code to validate its authenticity (that is, relying only on trusted digital signatures, the electronic equivalent of a trusted handwritten signature, on software that you have ... protecting represent ideal targets for this type of attack Protect your intrusion and vulnerability analysis systems Avoid administering your systems so that the protectors (intrusion detection...
- 44
- 197
- 0

Mission-Critical Security Planner When Hackers Won’t Take No for an Answer phần 3 pptx
Ngày tải lên :
13/08/2014, 22:21
... for Authorization and Access Control (continued) Authentication Summary To begin the summary for the Authentication element, I want to tell you about an actual situation that points out the seriousness ... implement them Remember: Administrator authentication is fundamental Your network authentication plan must specify how network administrators authenticate to network components (such as routers) The ... consider making it easier to be authenticated Architecturally, authentication is achieved through three system functions: Through registration Essentially, this is the act of granting trust to an individual...
- 44
- 295
- 0

Mission-Critical Security Planner When Hackers Won’t Take No for an Answer phần 4 ppsx
Ngày tải lên :
13/08/2014, 22:21
... solution Define the administrator-level authentication requirements to all infrastructure components The administrator-level authentication architecture for infrastructure components is one of the ... important to them and show them how improved authentication technology protects that information Put it in concrete, understandable terms At the same time, don t scare them too much about the existing ... and stored at the destination, the application and operating system control integrity, not the network If you want to maintain complete end-to-end integrity, you have to implement integrity mechanisms...
- 44
- 202
- 0

Mission-Critical Security Planner When Hackers Won’t Take No for an Answer phần 5 ppt
Ngày tải lên :
13/08/2014, 22:21
... together to filter out any packets destined for the telnet port (TCP port 23) It’s important to note that it’s not the best way to filter by explicitly disabling telnet (or any other protocol) by ... authentication information received from the customer into their workstation The customer’s private information, and the ability to act on that information, should not be available to the representative ... understand motivations Train operations staff to understand the motivation of this security element, especially as it relates to backup filtering and protection within the architecture INCIDENT RESPONSE...
- 44
- 246
- 0

Mission-Critical Security Planner When Hackers Won’t Take No for an Answer phần 6 ppsx
Ngày tải lên :
13/08/2014, 22:21
... it In my experience, the single biggest mistake made in configurationmanagement architectures is to implement a system that does not allow operators and administrators to the one thing that they ... port (e.g., unauthorized executable content that routinely operates in its own protocol space but can instead be tunneled through http) APPLICATION Stage and test executable content When it comes ... our testing and staging systems are in place for experimentation, often administrators must test a change on a live system Therefore, administrators have to be able to take configurations they...
- 44
- 202
- 0

Mission-Critical Security Planner When Hackers Won’t Take No for an Answer phần 7 potx
Ngày tải lên :
13/08/2014, 22:21
... that many alarm installers don t actually think about security They’re not security people; they are installers, and the faster they install, the faster they are on their way to the next customer.) ... licensing terms On the side, too many people integrate this software without adequately testing and understanding it Do not completely discount the prospect that, at some time, open software you ... though, this interface is often their first point of attack Identify the specific security measures you are taking to protect the administrative and management interface OPERATING SYSTEM Identify...
- 44
- 218
- 0

Mission-Critical Security Planner When Hackers Won’t Take No for an Answer phần 8 pps
Ngày tải lên :
13/08/2014, 22:21
... hackers often attack it first as a means to undermine your security and to better cover their tracks Intrusion-detection systems may rely on time as well to detect certain attack signatures 297 ... security plan with the new employee 315 316 Chapter BUSINESSPEOPLE: CUSTOMERS Let customers know of staff changes that affect them Staff management is relevant to customers only to the extent that ... Worksheet 4.46 Support Interface Worksheet 331 332 Chapter Testing, Integration, and Staging The testing and staging of security-related components is a common thread in this book, with three important...
- 44
- 183
- 0

Mission-Critical Security Planner When Hackers Won’t Take No for an Answer phần 9 ppt
Ngày tải lên :
13/08/2014, 22:21
... Web page) to the TradeAgent Server The TradeAgent Server encrypts the resource and returns it to the TradeAgent Client The TradeAgent Client decrypts the resource and returns it to the Web browser ... negotiating with hackers, thus they typically react poorly to extortion attempts Thieves are learning that the Internet offers a great deal of extortion potential: It provides the anonymity they ... coordination, trying to test the latest version of these products with the TradeWave software was often problematic In one case, the TradeAgent Client went through a full testing cycle with the beta version...
- 44
- 191
- 0

Mission-Critical Security Planner When Hackers Won’t Take No for an Answer phần 10 pot
Ngày tải lên :
13/08/2014, 22:21
... two different data inputs is approximately zero HTTP HyperText Transfer Protocol (HTTP) The protocol used to browse the Web HTTP uses TCP port 80 HTTPS HyperText Transfer Protocol (HTTP), when ... wish to communicate over the Internet The proxy server pretends to be the Web browser to the rest of the world (to the Internet), inserting its own IP address into packets instead of the internal ... Certificate authority (CA) A trusted third party (an organization) that signs certificates If you trust a particular CA, then you trust certificates that it has signed A CA can sign certificates issued...
- 37
- 334
- 0

Nghiên cứu tận dụng nhiệt từ khí xả động cơ reaseach to take full advantage of exhaust gas from engines
Ngày tải lên :
06/12/2012, 08:27
... có thi t bị trao đổi nhi t a) không hồi nhi t b) có hồi nhi t Hình Sơ đồ máy lạnh hấp thụ NH3/H2O TL: Van ti t lưu NT: Thi t bị ngưng t SH: Thi t bị sinh HT: Thi t bị hấp thụ • • • • BH: Thi t ... Bầu làm m t nước động Động Thi t bị ngưng t Thi t bị hấp thụ Thi t bị sinh Thi t bị bay 10 Van ti t lưu Năng su t lạnh chủ yếu phụ thuộc vào công su t động hệ số sử dụng nhi t thi t bị t n dụng, ... Ejector hiệu su t lại thấp đồng thời tuổi thọ t nh công nghệ không phù hợp điều kiện Vi t nam nên chọn máy lạnh hấp thụ t n dụng nhi t khí thải t u cá sử dụng môi ch t NH3/H2O hợp lí Ta chọn theo...
- 5
- 445
- 3

ADC KRONE - Hot Sheet - 10GBase-T - Competitive Comparison ADC vs. Panduit
Ngày tải lên :
04/11/2013, 11:15
... product specifications by contacting our headquarters office in Minneapolis ADC Telecommunications, Inc views its patent portfolio as an important corporate asset and vigorously enforces its patents ... are current as of the date of publication of this document Because we are continuously improving our products, ADC reserves the right to change specifications without prior notice At any time, you ... Product Feature ADC Product +/- +/- Panduit Comments COMPETITIVE COMPARISON Double Punching Two per termination point of same gauge (22 to 26 AWG) + - N/A Allows easy looping of stations for...
- 2
- 209
- 0

Tài liệu ADC KRONE - Hot Sheet - 10GBase-T - Competitive Comparison ADC vs. Panduit(Star) pptx
Ngày tải lên :
21/12/2013, 14:15
... product specifications by contacting our headquarters office in Minneapolis ADC Telecommunications, Inc views its patent portfolio as an important corporate asset and vigorously enforces its patents ... are current as of the date of publication of this document Because we are continuously improving our products, ADC reserves the right to change specifications without prior notice At any time, you ... Product Feature ADC Product +/- +/- Panduit Comments COMPETITIVE COMPARISON Double Punching Two per termination point of same gauge (22 to 26 AWG) + - N/A Allows easy looping of stations for...
- 2
- 236
- 0
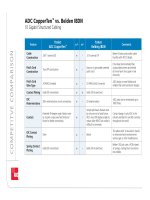
Tài liệu ADC KRONE - Hot Sheet - 10GBase-T - Competitive Comparison ADC vs. Belden docx
Ngày tải lên :
21/12/2013, 14:15
... specifications without prior notice At any time, you may verify product specifications by contacting our headquarters office in Minneapolis ADC Telecommunications, Inc views its patent portfolio ... used termination point (i.e 22 AWG to 26 AWG) ADC contact allows greater longevity and flexibility N/A Critical to ensuring no errors are placed on the network as a result of the cabling system (the ... stations for applications such as Local Talk IDC Contact Oxidation Does not corrode Silver tarnish is highly conductive + - Will tarnish, which is nonconductive Additionally, tarnish is soft...
- 2
- 243
- 0

Tài liệu ADC KRONE - Hot Sheet - 10GBase-T - Competitive Comparison ADC vs. Berk tek docx
Ngày tải lên :
21/12/2013, 14:15
... contacting our headquarters office in Minneapolis ADC Telecommunications, Inc views its patent portfolio as an important corporate asset and vigorously enforces its patents Products orfeatures ... publication of this document Because we are continuously improving our products, ADC reserves the right to change specifications without prior notice At any time, you may verify product specifications ... locations, please refer to our web site ADC Telecommunications, Inc., P.O Box 1101, Minneapolis, Minnesota USA 55440-1101 Specifications published here are current as of the date of publication...
- 2
- 260
- 0

Báo cáo khoa học: Oligomannose-coated liposomes efficiently induce human T-cell leukemia virus-1-specific cytotoxic T lymphocytes without adjuvant doc
Ngày tải lên :
14/03/2014, 23:20
... in postallogeneic stem cell transplantation patients The expression of Tax by the host cell targets them for attack by CTL, resulting in the elimination of the infected cell [32] However, the expression ... transplantation patients, which might account for the efficacy of this therapy [31] Therefore, the efficient induction of HTLV-1-specific CTL by OML ⁄ Tax could be adapted to prevent the relapse of ATL ... replacing Tax with antigens such as HBZ or tumor antigen, whereas OML ⁄ Tax could be adapted as a prophylactic for ATL and ATL patients expressing Tax In this study, we demonstrated that OML ⁄ Tax strongly...
- 9
- 243
- 0

it doesn't take a rocket scientist, great amateurs of science - malone
Ngày tải lên :
05/06/2014, 11:29
... then cover the buds with tiny caps of calico cloth, to protect them for the few 12 It Doesn t Take a Rocket Scientist days it would take for the female stigma to mature and become sticky The cap ... not a man with a large ego Those who 24 It Doesn t Take a Rocket Scientist would fight in his defense long after his death often had outsize egos, and reputations to protect, which meant that the ... of adults) whom he tried to turn on to the pleasures of astronomy It was true that his discoveries had gradually gained him a serious reputation among 44 It Doesn t Take a Rocket Scientist both...
- 231
- 162
- 0

Take my hand pdf
Ngày tải lên :
23/06/2014, 00:20
... some place to go Cause our hearts are locked forever And our love will never die Take my hand tonight One last time Take my hand tonight Let's not think about tomorrow Take my hand tonight We could ... hand tonight We could find some place to go Cause our hearts are locked forever And our love will never die (Love will never die) Take my hand tonight One last time ...
- 2
- 198
- 0
Tìm thêm:
- hệ việt nam nhật bản và sức hấp dẫn của tiếng nhật tại việt nam
- xác định các mục tiêu của chương trình
- xác định các nguyên tắc biên soạn
- khảo sát các chuẩn giảng dạy tiếng nhật từ góc độ lí thuyết và thực tiễn
- khảo sát chương trình đào tạo của các đơn vị đào tạo tại nhật bản
- khảo sát chương trình đào tạo gắn với các giáo trình cụ thể
- xác định thời lượng học về mặt lí thuyết và thực tế
- tiến hành xây dựng chương trình đào tạo dành cho đối tượng không chuyên ngữ tại việt nam
- điều tra đối với đối tượng giảng viên và đối tượng quản lí
- điều tra với đối tượng sinh viên học tiếng nhật không chuyên ngữ1
- khảo sát thực tế giảng dạy tiếng nhật không chuyên ngữ tại việt nam
- khảo sát các chương trình đào tạo theo những bộ giáo trình tiêu biểu
- nội dung cụ thể cho từng kĩ năng ở từng cấp độ
- xác định mức độ đáp ứng về văn hoá và chuyên môn trong ct
- phát huy những thành tựu công nghệ mới nhất được áp dụng vào công tác dạy và học ngoại ngữ
- mở máy động cơ lồng sóc
- mở máy động cơ rôto dây quấn
- các đặc tính của động cơ điện không đồng bộ
- hệ số công suất cosp fi p2
- đặc tuyến hiệu suất h fi p2