security assessment case studies for implementing the nsa iam phần 7 doc

security assessment case studies for implementing the nsa iam phần 7 doc
... questions
that will help the assessment team gain the needed information and identify the
organization’s vulnerabilities .The first resource for questions comes from the
security expertise of the assessment ... feedback from the departments that the assessment was
going better than they expected and that they found value in the information
that was being collected.Th...

security assessment case studies for implementing the nsa iam phần 1 docx
... drive the
assessment effort. Ultimately, the majority of information is the same in either
www.syngress.com
Laying the Foundation for Your Assessment • Chapter 1 3
Contracting and the NSA IAM
NSA ... of
performing assessments the way NSA does.
To recap, the IAM trains the individuals in the IAM standard, while the IA-
CMM appraises the organization’s ab...
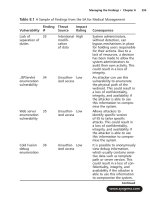
security assessment case studies for implementing the nsa iam phần 8 docx
... have to map the finding to the OICM, or can you just map it
to the SICM?
A: As you have already learned, the impact definitions are the same for both the
OICM and the SICM.Therefore, the findings ... client.They are now all on the same page when it comes to their critical
systems and critical information.They are all aware of the issues or vulnerabilities
they have within t...

security assessment case studies for implementing the nsa iam phần 2 ppt
... directly from
the integration of the organization’s mission with the IAM process and security
www.syngress.com
46 Chapter 2 • The Pre -Assessment Visit
Figure 2.1 The IAM Timeline: The Pre -Assessment ... phases of the IAM assessment.
This allows the assessment plan to be used as the scoping input for the
onsite assessment contract.
Understanding Scoping...

security assessment case studies for implementing the nsa iam phần 3 ppt
... have the appropriate pieces in place to create the OICM.This is
one of the primary deliverables of the IAM assessment; it defines much of the key
information that lays the foundation for the remainder ... the time the
IAM engagement gets into full swing, however, the main customer POC
is often the biggest proponent of the process.
Who Is the Assessment Team L...

security assessment case studies for implementing the nsa iam phần 4 pot
... 3:25 PM Page 1 07
In the majority of assessments, the values for each block within the SCMs
will be carried directly over from the OICM. Because of the top-down nature of
the NSA IAM, the OICM already ... the
columns across the top of the matrix with the names of the impact attributes
we’ll be using for the assessment. The rows are labeled along the left...

security assessment case studies for implementing the nsa iam phần 5 potx
... up the TAP, since it can be considered the core outcome of
the pre -assessment site visit .The TAP is the primary deliverable created during
the pre -assessment phase .The TAP combines all the information ... practices.
Understanding the Purpose
of the Technical Assessment Plan
The TAP document is designed to tie together all aspects of an IAM between the
customer...

security assessment case studies for implementing the nsa iam phần 6 pdf
... adjustments to the assessment approach to be able
to accomplish the effort
■
Reiterates the benefits of the assessment process
www.syngress.com
Customer Activities • Chapter 7 2 27
286 _NSA_ IAM_ 07. qxd 12/12/03 ... have the opportunity to return to home base and prepare for the onsite
portion of the assessment. The focus of the pre -assessment site visit and th...

security assessment case studies for implementing the nsa iam phần 9 pot
... conduct
the assessment. In our case, we describe the NSA IAM as the methodology used
to conduct the assessment and the basis for the assessment process. Since this is
the main document, the assessment ... anal-
ysis. Security Horizon utilized the National Security Agency (NSA) Information
Security Assessment Methodology (IAM) to conduct the organizati...

security assessment case studies for implementing the nsa iam phần 10 pot
... 393–394
concerns, 376 – 377
contract concerns, 373 – 375
control of, 372
customer documentation, 370
customer proprietary materials, 368–369
defined, 368
documentation by assessment team,
370 – 372
liability ... concerns, 375 – 376
public domain documentation, 369– 370
document-tracking templates, 411
documentation
determining location of, 172
in higher education case study, 177...
Từ khóa:
- are stimulated by extracellular matrix proteins such as type i collagen previous studies have demonstrated the involvement of a dggryy sequence located within the a1 chain cterminal telopeptide in type i collageninduced pmn activation
- spreadsheets and case studies
- issues and case studies
- tips for using the computer
- case studies in finance managing for corporate value solutions
- Nghiên cứu sự biến đổi một số cytokin ở bệnh nhân xơ cứng bì hệ thống
- Báo cáo quy trình mua hàng CT CP Công Nghệ NPV
- chuyên đề điện xoay chiều theo dạng
- Nghiên cứu sự hình thành lớp bảo vệ và khả năng chống ăn mòn của thép bền thời tiết trong điều kiện khí hậu nhiệt đới việt nam
- Nghiên cứu tổ hợp chất chỉ điểm sinh học vWF, VCAM 1, MCP 1, d dimer trong chẩn đoán và tiên lượng nhồi máu não cấp
- Nghiên cứu vật liệu biến hóa (metamaterials) hấp thụ sóng điện tử ở vùng tần số THz
- Giáo án Sinh học 11 bài 13: Thực hành phát hiện diệp lục và carôtenôit
- Giáo án Sinh học 11 bài 13: Thực hành phát hiện diệp lục và carôtenôit
- Phát triển mạng lưới kinh doanh nước sạch tại công ty TNHH một thành viên kinh doanh nước sạch quảng ninh
- Phát hiện xâm nhập dựa trên thuật toán k means
- Định tội danh từ thực tiễn huyện Cần Giuộc, tỉnh Long An (Luận văn thạc sĩ)
- Tìm hiểu công cụ đánh giá hệ thống đảm bảo an toàn hệ thống thông tin
- Thơ nôm tứ tuyệt trào phúng hồ xuân hương
- Thiết kế và chế tạo mô hình biến tần (inverter) cho máy điều hòa không khí
- Chuong 2 nhận dạng rui ro
- Tổ chức và hoạt động của Phòng Tư pháp từ thực tiễn tỉnh Phú Thọ (Luận văn thạc sĩ)
- Kiểm sát việc giải quyết tố giác, tin báo về tội phạm và kiến nghị khởi tố theo pháp luật tố tụng hình sự Việt Nam từ thực tiễn tỉnh Bình Định (Luận văn thạc sĩ)
- Tranh tụng tại phiên tòa hình sự sơ thẩm theo pháp luật tố tụng hình sự Việt Nam từ thực tiễn xét xử của các Tòa án quân sự Quân khu (Luận văn thạc sĩ)
- Giáo án Sinh học 11 bài 15: Tiêu hóa ở động vật
- Nguyên tắc phân hóa trách nhiệm hình sự đối với người dưới 18 tuổi phạm tội trong pháp luật hình sự Việt Nam (Luận văn thạc sĩ)